December 18th was a good day for hackers. WordPress websites was under highest brute force attack.
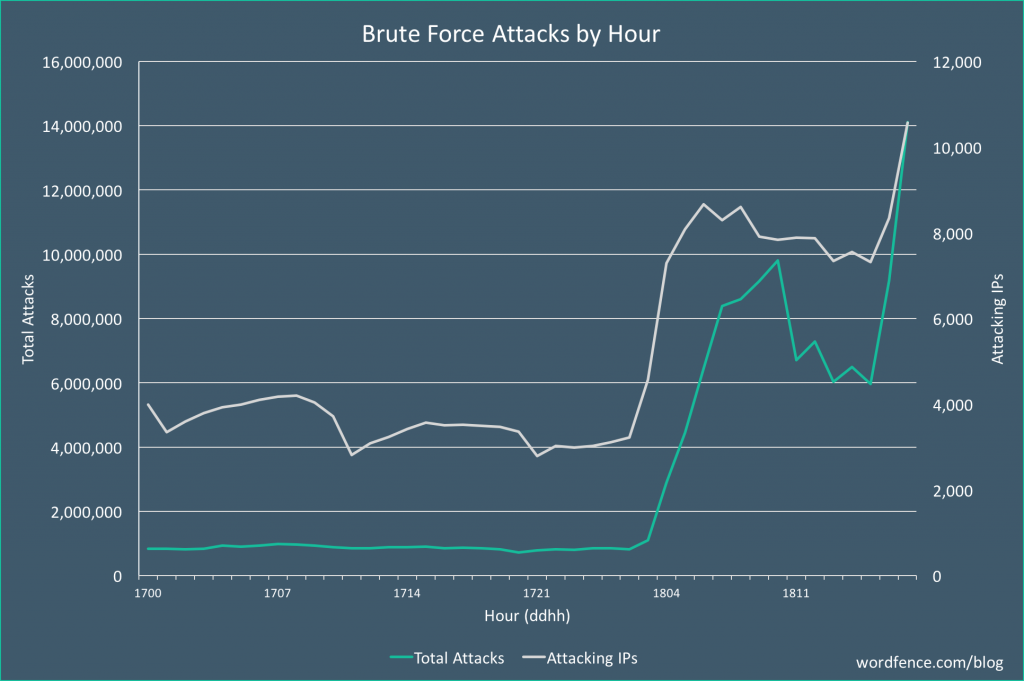
According to an analysis by researchers from website security firm Wordfence, this was the highest volume attack that Wordfence team have seen.
“This is the most aggressive campaign we have seen to date, peaking at over 14 million attacks per hour,” said Wordfence CEO and founder Mark Maunder on Monday.
“The attacker is using sophisticated malware to control compromised WordPress servers remotely. The servers are being used to both attack other WordPress sites and to mine for Monero, a cryptocurrency that can be efficiently mined using web server hardware.” explain attacks Wordfence team.
Also, on the begining of December, a huge database of hacked credentials was discovered. Seems it is related to the later December brute force attacks.
While 4iQ scanning the dark web for stolen, leaked or lost data, ” discovered a single file with a database of 1.4 billion clear text credentials — the largest aggregate database found in the dark web to date.
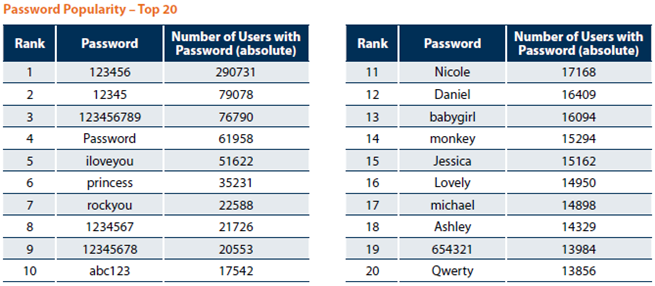
None of the passwords are encrypted, and what’s scary is we’ve tested a subset of these passwords and most of them have been verified to be true.”
Wordfence says that attackers use “a combination of common password lists and heuristics based on the domain name and contents of the site that it attacks.”
Using this new database that provides fresh credentials that, when matched with a WordPress username, hackers can have a higher success rate for attacking WordPress sites that do not have any protection.
So, we all need to protect our WordPress sites.
How to prevent a brute force attack?
Most brute force attacks work by targeting a website, typically the login page, with millions of username and password combinations until a valid combination is found.
The best methods for brute force protection we recommend:
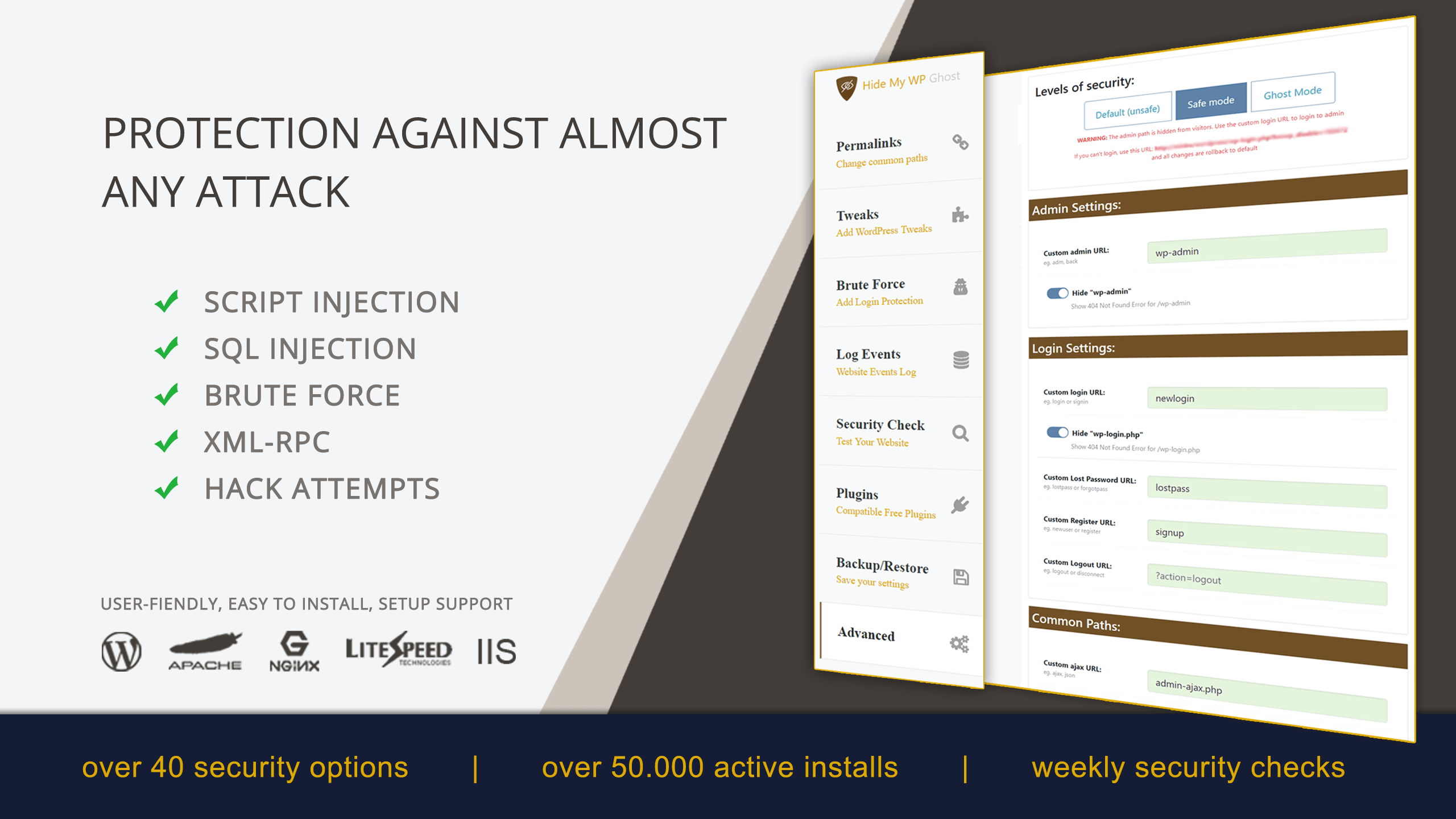
- Rename WordPress login URL to your website. You can do that with Hide my Wp Ghost Plugin.
- Change your admin username from the default ‘admin’ to something harder to guess.
- Verify if you have a strong password which includes Caps, Symbols and Numbers too. Do not reuse a password on multiple services.
- Disable XML-RPC protocol plugin
- Additionally, you can disable JSON API with Hide my Wp Ghost Plugin.
- Monitor login fail attempts with Hide my Wp Ghost Plugin Brute Force protection
- Safeguard Your Business with Hide My WP Lifetime Deal in 2023: Protecting Your Website from Hackers and Bots - June 5, 2023
- Protect Your WordPress Website From Hackers with Hide My WP Ghost – Save Money and Avoid Costly Repairs - March 23, 2023
- 4 Essential WordPress Plugins for Small Businesses from Squirrly - October 15, 2021


I have Jetpack and Limit Login attempts – are those effective in blocking the attacks?
Yes, Jetpack is blocking the attacks, the only problem with Jetpack is the loading time which is way too high for a plugin.