WordPress is one of the most popular CMS (Content Management System) on the internet these days. Around 26.6% of the websites are made in WordPress.
WordPress is known for being a very secure CMS and the software usually pushes updates to patch all the known vulnerabilities. However, third party themes and plugins make WordPress vulnerable. Sometimes hackers also find vulnerabilities in WordPress that allow them to hack the whole server.
Unfortunately, it is precisely its popularity that makes it such an appealing target.
Based on the recent report made by Sucuri, 78% of the hacked websites use WordPress CMS.
How is this possible?
Most site owners don’t know that the biggest risk comes from the installed plugins and themes.
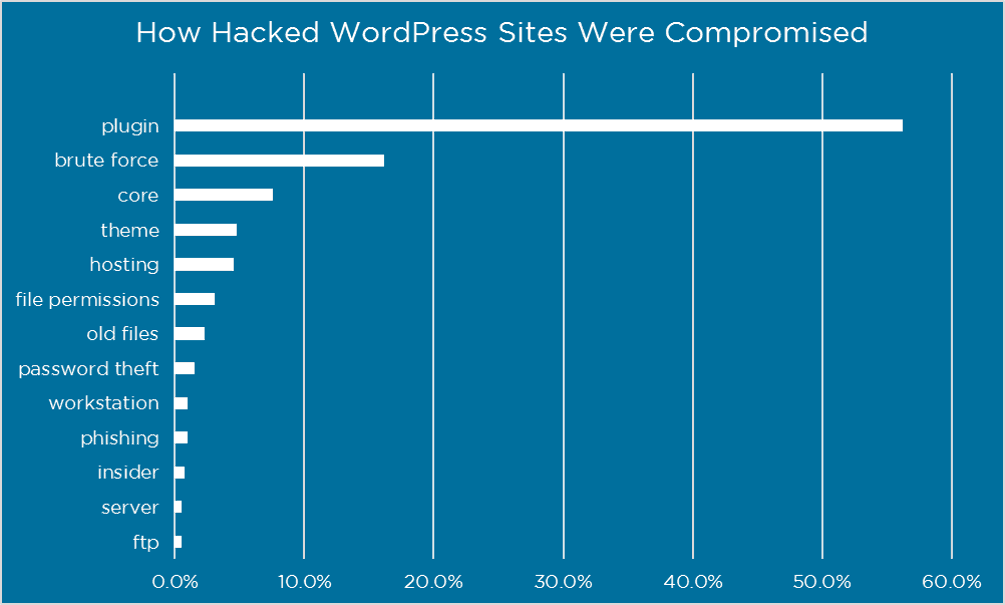
Source: wordfence
Plugins play a big part in making WordPress as notorious as it is today.
There are over 46,000 plugins available for download in the official WordPress directory. You obviously need to be careful with them, as plugin vulnerabilities represented 55.9% of the known entry points reported by respondents.
How do hackers get into my website through plugins and themes?
There are some well-known methods used by hackers bots to break a WordPress site:
- Brute Force Attacks
The most common way that hackers use to attack WordPress sites is with brute force attacks or HTTP requests.
Brute-force hackers use software to try to gain access to your website by guessing at your password until they get lucky and break in. Often, simple countermeasures like requiring CAPTCHA or 2-step verification on login can easily stop brute force login attempts in their tracks. - Path Traversal (know as “dot dot slash attack”)
This vulnerability allows an attacker to download any file from a WordPress server, including the wp-config.php file.
That data includes database credentials for the website and other information that could potentially enable an attacker to gain full control of the site.
The calls are usually like this:
GET /wp-config.php HTTP/1.0 Cookie: TEMPLATE=../../../../../../../../../wp-config.php - Script insertion
Another common category of hacker attacks is specially-crafted HTTP requests sent to your server.
These requests are designed to exploit specific vulnerabilities which are often caused by outdated or insecure software, themes, or plugins.
Anything contained in your wp-content directory, whether active or inactive, can potentially introduce security vulnerabilities to your website. Knowledgeable hackers can exploit such vulnerabilities to disable or gain access to your blog.
What are the options to protect my website?
If you’re not an expert in WordPress, we recommend you to install a safe/fast security plugin. To be sure you get support and updates, you should look for a premium plugin. There are some great WordPress security plugins on the market, and the prices are affordable.
To help you, we did the hard work, and we’ve tested many WordPress plugins this year (2017).
To make it even easier, all the plugins are tested and scored by security, speed, user experience, price, support and you can just select the ones that are suitable for your website.
- Name: Sucuri Security
- Security: High
- Average Speed: 0.03s
- User Experience: 6/10
- Support: Excellent Support
- Name: Hide My WordPress Ghost
- Security: Good
- Average Speed: 0.03s
- User Experience: 7/10
- Support: Excellent Support
- Name: Opt-In Content Locker
- Security: Good
- Average Speed: 0.12s
- User Experience: 7/10
- Support: Medium Support
Note: There are more security plugins in the queue. We check each plugin for an entire week before we post them in this article. Get back next week for more reviews.
- What changed when we started using WP Ghost - December 5, 2025
- WordPress REST API Security: Best Practices and Tools - June 24, 2024
- WordPress Firewalls & Tools for Your Website Security - June 17, 2024


all and sundry is doing seo, So ranking in seek engine is becoming hard day by day. thanks to your hints. I would like to implement some of them. Yoast is not completly unfastened I would like to have any other opportunity to yoast.