We measured the attacks before and after activating WP Ghost.
After we enabled the main protections, attack traffic dropped by about 99%. Hackers didn’t “become nicer”. Their bots simply stopped finding the usual weak spots on WordPress sites that WP Ghost hides and protects.
WordPress REST API Security: Best Practices and Tools
The WordPress REST API provides a powerful way to interact with your WordPress site using JSON-formatted data. It enables developers to create applications that can perform various tasks, such as retrieving posts, updating user profiles, and more. However, with great power comes great responsibility.
Securing the WordPress REST API is crucial to protect your site from potential threats. In this article, we will explore the importance of REST API security, common vulnerabilities, and best practices to enhance the security of your WordPress site.
Understanding the WordPress REST API
What is the WordPress REST API?
The WordPress REST API allows developers to interact with WordPress sites remotely by sending HTTP requests and receiving JSON responses. This API can be used to build custom themes, plugins, mobile applications, and more, providing a flexible and powerful way to extend the functionality of WordPress.
Why Secure the REST API?
While the REST API opens up new possibilities for developers, it also exposes your site to potential security risks. If not properly secured, malicious actors can exploit vulnerabilities to gain unauthorized access to your site, steal sensitive data, or perform malicious actions. Therefore, it is essential to implement robust security measures to protect your site.
Common Vulnerabilities in the WordPress REST API
Unauthorized Access
One of the primary concerns with the REST API is unauthorized access. If endpoints are not properly secured, attackers can access sensitive information or perform actions without proper authentication.
Data Exposure
The REST API can expose more data than intended, especially if the default settings are used. Sensitive information, such as user details and private posts, can be unintentionally exposed through publicly accessible endpoints.
Rate Limiting
Without proper rate limiting, the REST API can be abused by attackers to perform brute force attacks or overload your server with excessive requests, leading to performance issues or downtime.
Best Practices for Securing the WordPress REST API
Implement Authentication and Authorization
Use Nonce Verification
Nonces are unique tokens that can be used to verify the authenticity of requests. Implementing nonce verification ensures that requests to the REST API are legitimate and helps prevent CSRF (Cross-Site Request Forgery) attacks.
Use OAuth
OAuth is an open standard for access delegation, commonly used as a way to grant websites or applications limited access to a user’s data without exposing passwords. Implementing OAuth for your REST API endpoints ensures that only authenticated users can access or modify data.
Restrict API Access
Disable REST API for Unauthorized Users
To prevent unauthorized access, you can disable the REST API for users who are not logged in. This ensures that only authenticated users can interact with your API.
add_filter('rest_authentication_errors', function($result) {
if (!empty($result)) {
return $result;
}
if (!is_user_logged_in()) {
return new WP_Error('rest_not_logged_in', 'You are not currently logged in.', array('status' => 401));
}
return $result;
});Limit Data Exposure
Ensure that only the necessary data is exposed through the REST API. Review and customize the endpoints to limit the amount of data returned, especially sensitive information.
Implement Rate Limiting
To prevent abuse of the REST API, implement rate limiting to restrict the number of requests that can be made within a specific time period. This helps protect your site from brute force attacks and reduces the load on your server.
Monitor and Log API Activity
Monitoring and logging API activity can help you detect and respond to suspicious behavior. Keep an eye on the API request logs to identify potential security threats and take appropriate action.
Use Security Plugins
Leverage security plugins designed to enhance the security of your WordPress site and the REST API. Some popular security plugins include:
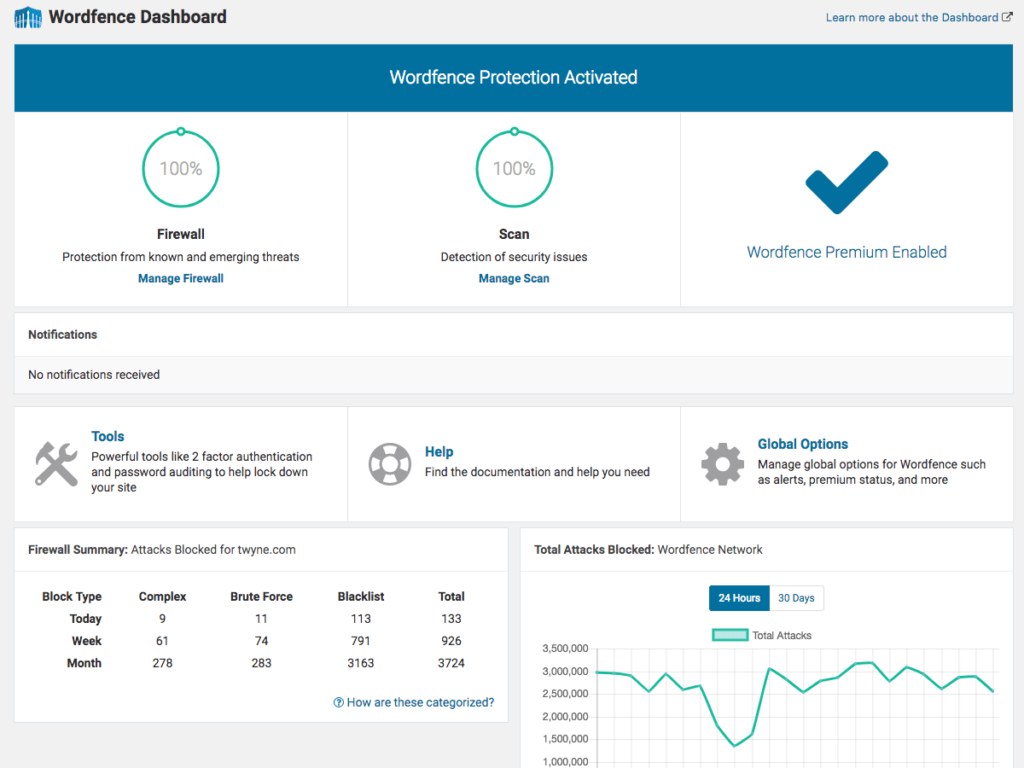
- Wordfence Security: Provides comprehensive security features, including a firewall, malware scanner, and protection for the REST API.
- Solid Security: Offers various security measures, such as brute force protection, two-factor authentication, and REST API security settings.
- Sucuri Security: Provides website security services, including malware scanning, security audits, and REST API protection.
- Hide My WP Ghost: Conceals common WordPress paths and enhances the security of the REST API by hiding potential vulnerabilities and offering additional security measures.
Use HTTPS
Ensure that your WordPress site uses HTTPS to encrypt data transmitted between the client and the server. This helps protect sensitive information, such as authentication tokens and user data, from being intercepted by attackers.
Regularly Update WordPress and Plugins
Keep your WordPress core, themes, and plugins up to date with the latest security patches. Regular updates help protect your site from known vulnerabilities and ensure that you are using the most secure versions of the software.
Advanced Techniques for REST API Security
Custom Authentication Methods
For more advanced security requirements, consider implementing custom authentication methods. For example, you can use JWT (JSON Web Tokens) to secure your REST API endpoints. JWTs provide a secure way to transmit information between parties and can be used to verify the identity of users making API requests.
Endpoint Whitelisting
Limit access to specific IP addresses or domains by implementing endpoint whitelisting. This ensures that only trusted sources can interact with your REST API.
add_filter('rest_authentication_errors', function($result) {
if (!empty($result)) {
return $result;
}
$allowed_ips = array('123.456.789.000', '987.654.321.000');
if (!in_array($_SERVER['REMOTE_ADDR'], $allowed_ips)) {
return new WP_Error('rest_forbidden_ip', 'Your IP address is not allowed to access this endpoint.', array('status' => 403));
}
return $result;
});Role-Based Access Control (RBAC)
Implement role-based access control to restrict access to specific endpoints based on user roles and permissions. This ensures that only authorized users can perform certain actions through the REST API.
Encrypt Sensitive Data
Encrypt sensitive data before transmitting it through the REST API. This adds an additional layer of security, ensuring that even if data is intercepted, it remains protected.
Conclusion
Securing the WordPress REST API is crucial for protecting your website from potential threats and ensuring the integrity of your data. By implementing best practices such as authentication, authorization, rate limiting, and monitoring, you can significantly enhance the security of your REST API. Additionally, leveraging security plugins and advanced techniques can provide further protection against sophisticated attacks.
Investing time and resources into securing your WordPress REST API not only protects your site but also builds trust with your users, ensuring a safe and reliable online experience. With the right tools and practices, you can stay one step ahead of cyber threats and keep your website secure.
The Importance of WordPress Security Checks
WordPress security is a critical concern for website owners and administrators. Regular WordPress security checks are essential to protect your site from threats and vulnerabilities. One effective way to enhance your site’s security is by using the security check features available in security plugins.

- Why Regular WordPress Security Checks are Essential
- 1. Safeguarding Sensitive Information
- 2. Maintaining Site Performance and Integrity
- 3. Enhancing User Trust and Experience
- 4. Preventing Costly Downtime
- 5. Complying with Legal and Regulatory Requirements
- How to Perform a WordPress Security Check with Hide My WP Ghost
- Steps to Perform a Security Check
Why Regular WordPress Security Checks are Essential
1. Safeguarding Sensitive Information
WordPress websites often handle sensitive information, such as user credentials, personal data, and payment details. Regular security checks help identify and address potential vulnerabilities that could expose this sensitive information to unauthorized parties.
2. Maintaining Site Performance and Integrity
A compromised site can lead to the injection of malicious code, slowing down your site or causing it to crash. Security checks ensure your website remains free of malware and other malicious code, maintaining optimal performance and site integrity.
3. Enhancing User Trust and Experience
Users expect a secure browsing experience. A security breach can significantly damage your reputation and erode user trust. By conducting regular security checks, you demonstrate a commitment to protecting user data, thereby enhancing trust and providing a secure experience.
4. Preventing Costly Downtime
Security breaches can lead to significant downtime, affecting your site’s availability and potentially leading to a loss of revenue. Regular security checks help mitigate this risk by addressing vulnerabilities before they can be exploited, ensuring your site remains operational.
5. Complying with Legal and Regulatory Requirements
Many jurisdictions have legal requirements for data protection and security. Regular security checks help ensure your site complies with these regulations, avoiding potential fines and legal issues.
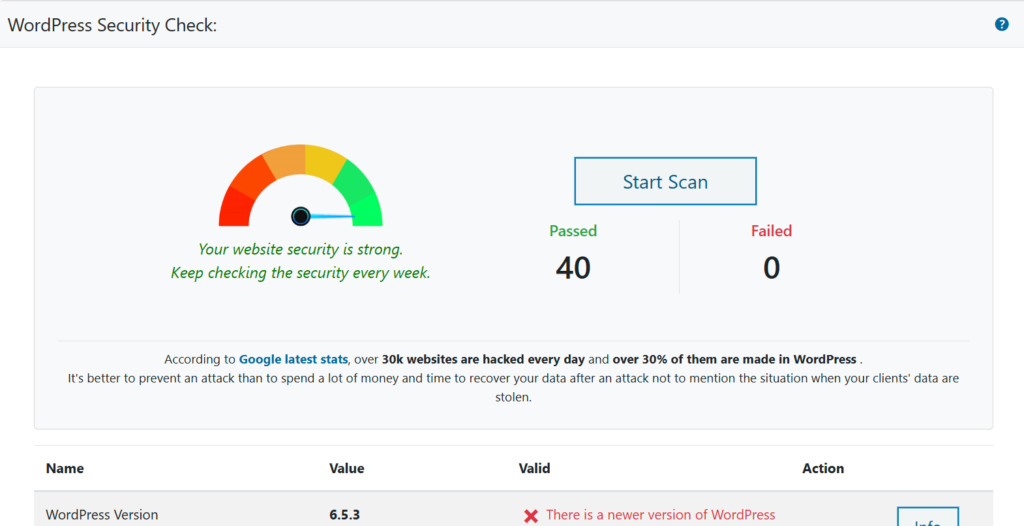
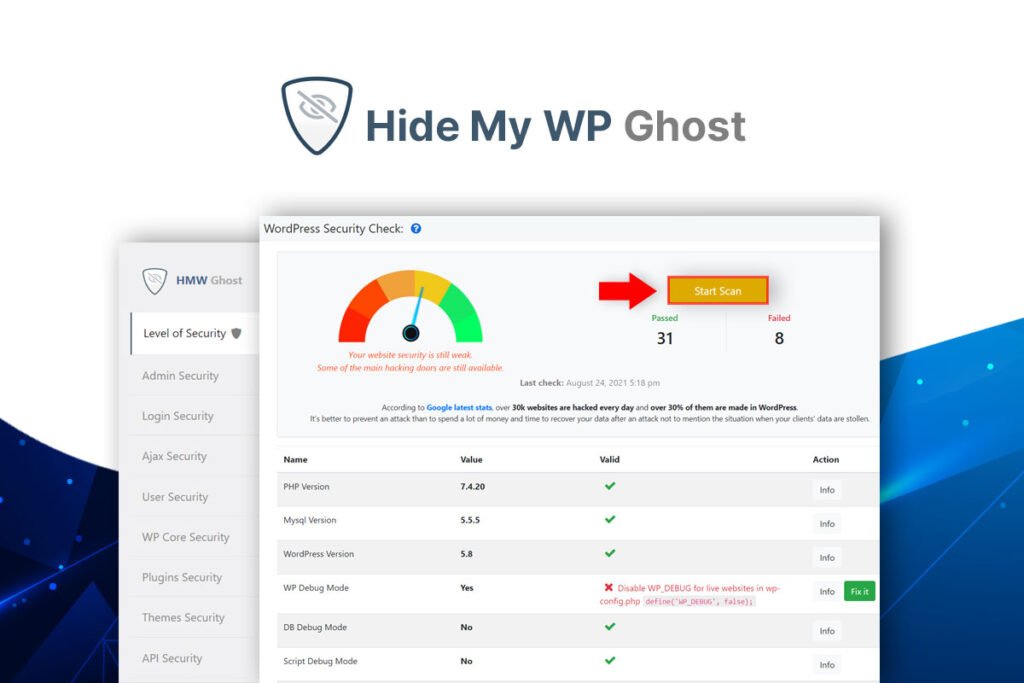
How to Perform a WordPress Security Check with Hide My WP Ghost
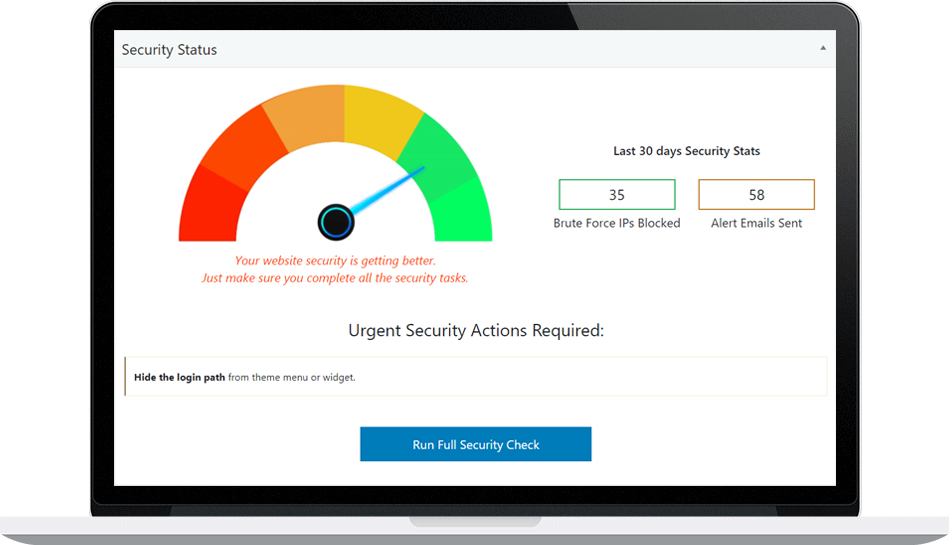
Hide My WP Ghost is a comprehensive security plugin designed to protect WordPress sites from common threats. The Security Check feature in Hide My WP Ghost provides a thorough assessment of your site’s security status, identifying vulnerabilities and offering actionable recommendations to enhance security.
Steps to Perform a Security Check
- Install and Activate Hide My WP Ghost: Begin by installing and activating the Hide My WP Ghost plugin on your WordPress site.
- Navigate to the Security Check Feature: Go to Hide My WP > Security Check in your WordPress dashboard.
- Run the Security Check: Click on the ‘Run Security Check’ button to initiate the process. The plugin will scan your site for potential vulnerabilities and provide a detailed report.
- Review and Implement Recommendations: Review the security check report and implement the recommended actions to enhance your site’s security.
For more detailed instructions and information, visit the Hide My WP Ghost knowledge base.
Regular WordPress security checks are vital for maintaining the security and integrity of your website. They help protect sensitive data, enhance user trust, prevent downtime, and ensure compliance with legal requirements.
Utilizing tools like Hide My WP Ghost makes it easy to conduct comprehensive security checks and safeguard your site against potential threats. Don’t wait until it’s too late—start performing regular security checks today to keep your WordPress site secure.
How to Secure a WordPress Database: Essential Tips for Site Owners
Ensuring the security of your WordPress database is crucial to protecting your website from potential threats. Your database contains all your site’s data, including posts, user information, and other essential content. If compromised, it can lead to significant issues, including data loss, unauthorized access, and more. In this article, we will explore the most effective ways to how to secure a WordPress database, providing you with actionable tips to safeguard your site.

- 1. Why Securing Your WordPress Database is Important
- 2. Use a Strong Database Password
- 3. Change the Default Table Prefix
- Steps to Change the Table Prefix:
- 4. Limit Database Access
- 5. Regularly Back Up Your Database
- 6. Use SSL to Encrypt Data
- 7. Implement Database Activity Monitoring
- 8. Regularly Update WordPress and Plugins
- 9. Utilize Security Plugins
1. Why Securing Your WordPress Database is Important
Your WordPress database is the backbone of your website. It stores all of your content, user information, and site settings. Without proper security measures, it becomes vulnerable to attacks, which can lead to:
- Data Theft: Hackers can steal sensitive information.
- Data Loss: Important data might be deleted or corrupted.
- Site Downtime: Your site could become inoperable.
- SEO Damage: Your search engine rankings can suffer.
By implementing robust security measures, you can prevent these issues and ensure your website remains safe and operational.
2. Use a Strong Database Password
A strong database password is your first line of defense. Ensure that your database password is:
- Unique: Do not use the same password across multiple sites.
- Complex: Include a mix of uppercase and lowercase letters, numbers, and special characters.
- Long: Aim for at least 12 characters.
Consider using a password manager to generate and store strong passwords.
3. Change the Default Table Prefix
By default, WordPress uses the prefix wp_ for all database tables. Hackers are aware of this and often target these tables. Changing the table prefix to something unique can add an extra layer of security. For example, you could change it to wpsecure_123.
Steps to Change the Table Prefix:
- Backup Your Database: Always backup before making changes.
- Update wp-config.php: Change the
$table_prefixvariable. - Rename Tables: Use a plugin like WP-DBManager or a tool like phpMyAdmin to rename your tables.
Or run a security check in Hide My WP Ghost plugin and change the database prefix with just one click.
4. Limit Database Access
Only allow access to your database from trusted sources. You can achieve this by:
- Restricting Database User Privileges: Grant only the necessary privileges to each user.
- Limiting Host Access: Only allow specific IP addresses to access your database.
5. Regularly Back Up Your Database
Regular backups are essential. In case of a security breach, a recent backup allows you to restore your database to its previous state with minimal data loss. Use plugins like UpdraftPlus or BackupBuddy to automate your backups.
6. Use SSL to Encrypt Data
SSL (Secure Sockets Layer) encrypts the data transferred between your website and its visitors. It also encrypts the data between your WordPress site and the database. Ensure your hosting provider supports SSL, and obtain an SSL certificate for your site.
7. Implement Database Activity Monitoring
Monitoring your database for unusual activity can help you detect and respond to potential threats quickly. Tools like Sucuri and Wordfence can help you monitor and log database activity.
8. Regularly Update WordPress and Plugins
Keeping your WordPress core, themes, and plugins up to date is vital for security. Updates often include security patches for vulnerabilities. Set up automatic updates where possible to ensure you are always running the latest versions.
9. Utilize Security Plugins

Security plugins can provide an additional layer of protection. Consider using plugins like Hide My WP Ghost to enhance your site’s security. These plugins can help obfuscate vulnerabilities, monitor activity, and block malicious attempts.
Securing your WordPress database is an ongoing process that requires vigilance and regular maintenance. By following these tips, you can significantly reduce the risk of your site being compromised. Remember, a secure database is the foundation of a secure website.
For more advanced security solutions and continuous protection, consider using comprehensive security plugins like Hide My WP Ghost. These tools provide robust protection and peace of mind, allowing you to focus on creating great content without worrying about security threats.
By taking these steps, you can enhance the security of your WordPress database and protect your valuable data from potential threats. Stay proactive and keep your site secure!
Protect Your WordPress Website From Hackers with Hide My WP Ghost – Save Money and Avoid Costly Repairs
As a website owner, there are few things more stressful than finding out that your website has been hacked. It can be a frustrating and expensive experience, but there are steps you can take to avoid it. One such step is using a WordPress security plugin like Hide My WP Ghost.
Hide My WP Ghost is a powerful WordPress security plugin that can help protect your website from a wide range of hacker attacks. According to their website, the plugin adds filters and security layers to prevent Script and SQL Injection, Brute Force attacks, XML-RPC attacks, and more. By using this plugin proactively, you can save money by avoiding costly repairs after your website has been hacked.

WordPress websites are frequently targeted by hackers, and the numbers are staggering. According to a report by Sophos, at least 13,000 WordPress websites are hacked every day. That’s around 9 per minute, 390,000 per month, and 4.7 million per year! These attacks can be devastating for website owners, leading to lost revenue, damaged reputation, and significant cleanup costs.
With Hide My WP Ghost, you can take a proactive approach to website security and avoid these costly consequences. The plugin is easy to install and use, and it provides a wide range of security features to protect your website from attacks. For example, it can hide the fact that you are using WordPress, making it more difficult for hackers to target your site. It can also block malicious IP addresses, prevent directory browsing, and much more.
One of the best things about Hide My WP Ghost is that it is constantly updated to stay ahead of the latest hacker techniques. The plugin’s developers are constantly monitoring the latest threats and updating the plugin to provide the best possible protection for your website. This means that you can have peace of mind knowing that your website is always protected against the latest threats.
Another benefit of using Hide My WP Ghost is that it is an affordable way to protect your website. When you consider the potential cost of a hacked website, the price of the plugin is a small investment. By using Hide My WP Ghost proactively, you can avoid the much larger cost of cleaning up a hacked website and potentially losing customers and revenue.
In conclusion, if you are a WordPress website owner, you need to be aware of the constant threat of hacker attacks. By using a security plugin like Hide My WP Ghost, you can take a proactive approach to website security and avoid the costly consequences of a hacked website. With its easy installation and use, constant updates, and affordable price, Hide My WP Ghost is an excellent choice for website owners who value their online security. Don’t wait until it’s too late – protect your website today!
5 Things You Can Do To Protect Your Sites From Hackers
If you’re reading this post, you might have a question: Is WordPress secure?
WordPress is infamous for its vulnerabilities. Part of the problem arises from WordPress being so popular. Many hackers in the world try their hands on it.
But the truth is outdated WordPress versions, hacked themes or plugins and poor security practices are more likely the culprits. Nulled plugins often provide a login to WordPress backend allowing hackers to exploit the system as they wish. One way to ensure you don’t run into trouble with plugins is by downloading them directly from the source — just like this form builder plugin.
WordPress powers over 35.2% of all websites and it’s easy to see why so many vulnerabilities exist owing to the huge number of plugins and themes just sitting out there.
WordPress however also has the biggest team of experts keeping it safe and releasing updates and patches now and then. The core software gets updated now and then.
So here’s what you can do to protect your site.
1. Always Upgrade to the Latest PHP Version
PHP is the language WordPress is built on. For the proper upkeep of your site upgrading to the latest version of PHP is of the essence.
Know this: every major release gets to years of bug fixes and security updates.
So, the older your PHP version is, the more prone it is to being hacked.
As such, it’s important to keep your website constantly updated and do a website redesign from time to time to integrate these changes.
2. Change your WordPress login URL

When you log in you might have noticed the login URL is youdomain.com/wp-admin. This is the default login address and the whole world knows this including bots and scripts.
If you change this default URL you can better protect against brute force attacks. Remember that this doesn’t give some super immunity but it is a little trick. Hide my Wp Ghost does this wonderfully by changing the default login option not only for wp-admin but lots of other common paths.
Use the Hide my wp ghost plugin. It’s something unique that’s different from the words a bot usually scans for and attempts to login via brute force.
3. Limit Login Attempts

In addition to this, attempting the number of allowed login attempts is another thing you can do to effectively bypass the system.
Change your login URL to stem to the number of brute force login attempts. Also setting a number on the number of trial logins can help reduce the number of attempts by setting up lockout durations in place, the actual number of login attempts, and set IP whitelists and blacklists.
Which plugin to use for this? Hide My WP Ghost or Limit Login Attempts Reloaded is a great plugin that can help. Another plugin that does this more effectively is the Login Lockdown plugin.
With each failed login attempt the plugin notes down the IP address and the timestamps the login attempts.
If multiple attempts are attempted from the same IP range the login requests from that IP are blocked for future attempts.
4. Use WordPress Security Plugins

If you use security plugins they are known to make your WordPress site much more secure and safe.
There are tons of security plugins like Wordfence, Sucuri who work together to keep your website secure.
5. Invest in Secure WordPress Hosting

When it is about your site’s security you can’t simply trust cheap hosting.
There are many WordPress hosts that provide only some basic security coverage.
If you’re in a managed hosting then they manage the entire thing at their end and keep your site extremely secure to use. A host that you can trust is the foremost thing to choose from.
Server hardening is the first step to maintaining a safe and secure environment. Multiple layers of software and physical hardware is of importance to protecting against sophisticated virus attacks.
Servers on WordPress need to be always tested for different vulnerabilities with security flaws locked in. NGINX and OpenSSL often have vulnerabilities that need to be scanned. A cheap host can barely pay their upkeep bills let alone invest in the best hardware and software infrastructure. So, your site may end up getting hacked for no fault of yours.
Firewalls and hack detection systems should be in place to protect the site that installs WordPress and keep it protected during site construction. The server should also use secure networking and use secured file transfer portions such as sFTP.
Ending Thoughts
Whether you work from home or in an office, there are a number of ways to keep your WordPress site secure and manage all things in one place. With these tips, you will be able to keep the site running properly without any big issues. Take time and implement these security best practices so that you don’t run into trouble later on.
What is 503 Service Unavailable Error and How to Fix It
Error 503 Service Unavailable indicates that the webserver is temporarily unable to process the request. This can be a web server that you are trying to access directly, or another server, which in turn is trying to access a web server. It is called error 503 because it is the HTTP status code used by the webserver to detect such an error. The error can occur for several reasons, but the two most common reasons are: the server is overloaded with requests or maintenance is being performed.
6 WordPress Security Tips for New Bloggers
The excitement of owning a blog often comes with a price for newest bloggers. They often forget about the security of their content or already existing websites. This leads to loss of revenue, a drop in trust levels, and eventually hacking.
WordPress powers more than 33% of websites in the world, making it the most popular CMS likely to prone to security attacks. However, WordPress, on its own, is secure. It is the use of various plugins, themes, and some hosting, which make our WordPress sites vulnerable to security attacks.
As a beginner, there are a few things you could do to secure your site. To ensure your site is well functioning and protected from any attack, below are a few security tips that will guide you into understanding more about security attacks and their rightful cure – prevention.

1. Install a Plugin
The first step in securing your site is by installing a WordPress plugin. It is a primary step, but the logic in protecting the security of your site against security attacks and hacks. While there are a lot of plugins for use, opt for WordPress plugins as they’re more suitable with the site.
When installing the plugin, however, some factors should be kept in consideration to get the most out of it.
- A good plugin should be from a reliable source, preferably a WordPress plugins or from a site WordPress has deemed safe. Plugins from unknown websites are prone to attacks and hacks.
- Select a plugin of a considerable cost. Not every free plugin is safe to use. Or when in a budget, you opt for the cheapest because that’s what you can afford. Carefully analyze the price and invest in a good plugin.
- Choose a plugin with the right documentation. Before installing a plugin on your site, ensure you’ve read all its documentation and carefully checked for its authenticity. Also, there are reviews about a plugin on the internet. Please read them and see other people’s opinions, then make a choice.
Other helpful plugins may be of great help in improving the quality of content on your blog.
- Use a Complex Login Password
The popular way of hacking into someone’s site is by hacking their password. This gives you access to their files and site settings, making it easy for hackers to tamper with the settings and install malicious plugins or add backlinks.
Ackerman Steve, a researcher at TopEssayWriting and writer with ClassyEssay says, ‘Always use complex passwords to avoid cracking by hacker bots. To make a password powerful, add special characters other than letters to the composition of your password. Keep changing it frequently, over some time. It is advisable to use password managers to help you improve your password security.’
To boost your complex password, install plugins that will record all failed login attempts. The plugin will, after a particular number of failed logins from an IP, blacklist it thus, preventing any attack.
3. Two-Factor Authentication
Other than setting a complex password, setting up a two-factor authentication will help prevent your login from being compromised. The two-factor authentication will ensure that only authorized persons access your site. It is an essential tip as it provides another wall of defense in preventing security attacks and hackers.
Other than two-factor authentication, there is to assigning the least principles. When you assign a new person your password, you limit the activities they could do in your site. The login is only comprehensive for a few features and not each feature, which could allow for tampering of settings, plugins, and settings.
Let’s say your WordPress blog is for sharing stories. You’ve hired a new editor whom you wish to edit your stories. With the assigning of the least principles, you can limit their access to editing of the stories in your blog, nothing more. Providing limited access to your site gives you the ultimate control.
4. Manage Your Themes and Plugins
As mentioned earlier in this article, installing plugins from unknown sources have a higher risk of being malicious. It also applies to the themes you use for your WordPress site.
Before setting up a plugin or theme, check its authenticity, and determine its credibility. Check for its documentation and ensure that it is suitable for your WordPress. Using plugins and themes that aren’t suitable makes it easy for security attacks and hackers.
Madison Maupassant, a writer with BeGraded and essayist with Studyker opines, ‘Always ensure that your WordPress version is updated to the latest version. With every update, there are fixed bugs and new features that improve the security of your site. This also applies to themes and plugins always check to upgrade to the latest version.’
When updating configurations of plugins and themes on your site, they should be set manually by you. Sometimes settings can be less secure than when you manually set. When setting up manually, go through every instruction to see what needs to be changed.
5. Back-Up Regularly
With the internet, nobody is ever sure. To feel more secure, create a habit of regularly backing up your data as anything could happen. You can do so manually or the use of WordPress Backup Solution or any other software.
You can use a WordPress Backup Solution, or link up with a 3rd party backup system supported by WordPress. It is advisable to have at least two copies of your data at all times on different servers. This is because some backup servers can also be hacked.
6. Use Web Application Firewall (WAF)
There is a firewall that exists between your hosting server and network traffic. It prevents most common threats from reaching and destroying your WordPress site. It acts as a filter that protects your host system.
Web Application Firewall (WAF) detects and identifies the following threats: Cross-site scripting attacks, SQL injection attacks, and session hijacking. It is a highly recommended WordPress security feature, preferably for sites meant for business.
The most common firewalls you can use on WordPress are as follows:
- At the network level – it works on the network level when you’re hosting WordPress data on a center your own. It is costly and used by enterprise-level websites that have physical space for server installation.
- At the host level – it works on a web-application level, your WordPress. Your host does the lifting of filtering out traffic.
- Cloud-based WAF- it filters the most common threats before they hit your WordPress server. It is the most economical and easy to use.
In conclusion, the security of your WordPress site isn’t a compromise.
WordPress security is essential, and as a new blogger, it should be your top priority to have the best protection for your site. The above tips will go a long way in securing your site.